Discover New Bug Bounty Angles with Leaked Data

Bug bounty hunting has become a sophisticated field where hunters need to stay updated with new techniques and approaches. Leveraging leaked credentials and stealer logs, combined with Open-Source Intelligence (OSINT) tools, can provide a significant advantage. This post dives deep into what leaked credentials and stealer logs are, how to find valuable assets with OSINT tools, and highlights critical SaaS services and CI/CD pipeline tools to target. Additionally, we will discuss nuances such as redirection to Microsoft for authorization and the importance of enumerating paths for hidden login pages. A detailed report template for submission will also be provided.
What Are Leaked Credentials and Stealers?
Leaked credentials are sets of login details that have been exposed due to data breaches or malware logs. Stealer malware is designed to collect information from compromised systems, such as usernames, passwords, and cookies. These credentials often surface on dark-web forums and marketplaces, presenting both risks and opportunities for security professionals.
Incorporating leaked credentials into your bug bounty work—ethically and within program policies—can help you identify high-value vulnerabilities, especially when combined with detailed OSINT enumeration.
Increase Your Impact with OSINT Tools
OSINT tools can reveal exposed services and applications that might be overlooked. By integrating OSINT with leaked credential analysis, you can uncover assets such as SaaS instances and CI/CD platforms. Below are key tools and techniques:
Top OSINT Tools and Techniques:
- Subfinder: Discovers subdomains related to a target (e.g.,
admin.<targetdomain>.com,jira.<targetdomain>.atlassian.net). - Fofa: Searches for exposed services like Jira and GitLab. Use targeted queries such as
domain="atlassian.net"ortitle="GitLab". - Shodan: Scans for exposed devices and services. To find login panels and services, use specific search terms such as
http.title:"Jira"andhostname:"atlassian.net". - Amass: Maps subdomains and identifies exposed services like
ci.<targetdomain>.com. - Censys: Indexes internet-connected assets, helping locate exposed service panels.
- ffuf and GoBuster: These tools are invaluable for brute-forcing directories and paths. Enumerating login paths (e.g.,
/login,/admin,/login.do) can reveal hidden or secondary login portals, especially when SaaS tools require a redirect to Microsoft for SSO (Single Sign-On) authentication.
Redirection to Microsoft for Authorization
In some cases, SaaS services are configured to redirect users to Microsoft for authentication through Azure AD or other identity providers. This adds an extra layer of complexity but can be a strong indicator of other accessible login endpoints that bypass the standard Microsoft flow.
Key Points:
- When encountering such redirection, look for alternate paths and login pages that might not be protected by SSO.
- Use ffuf and GoBuster to enumerate directories and detect hidden login pages. Common paths include
/login,/admin,/login.do,/auth, and/user.
Example Command:
ffuf -u https://company.atlassian.net/FUZZ -w /path/to/wordlist.txt -mc 200,302
Examples of High-Value SaaS Panels and CI/CD Tools
Below are examples of SaaS platforms and CI/CD tools that bug bounty hunters should target. These tools often contain critical data and are commonly found on subdomains like company.<saastool>.com.
SaaS Panels:
- Jira (
company.atlassian.net): Exposes project management and issue tracking data. - Confluence (
confluence.company.atlassian.net): Reveals internal documentation and sensitive details. - ServiceNow (
company.servicenow.com): Contains service management and configuration information. - Salesforce (
company.salesforce.com): Can reveal customer data and CRM records. - Bitbucket (
company.bitbucket.org): Hosts source code and deployment configurations. - Slack (
company.slack.com): Includes team communication and shared access tokens. - Okta (
company.okta.com): If compromised, could affect authentication processes. - HubSpot (
company.hubspot.com): Marketing data, leads, and customer interactions.
CI/CD Pipeline Tools:
- Jenkins (
jenkins.company.com): Contains build and deployment configurations. - GitLab CI/CD: Integrated with GitLab for automated build and deployment.
- TeamCity (
teamcity.company.com): Automated build tool that may expose sensitive configurations. - Travis CI: Popular for automating builds and tests; check for environment variables.
- CircleCI (
circleci.company.com): Exposed pipelines can contain environment secrets. - Azure DevOps (
company.visualstudio.com): Comprehensive tool for managing code, builds, and deployments.
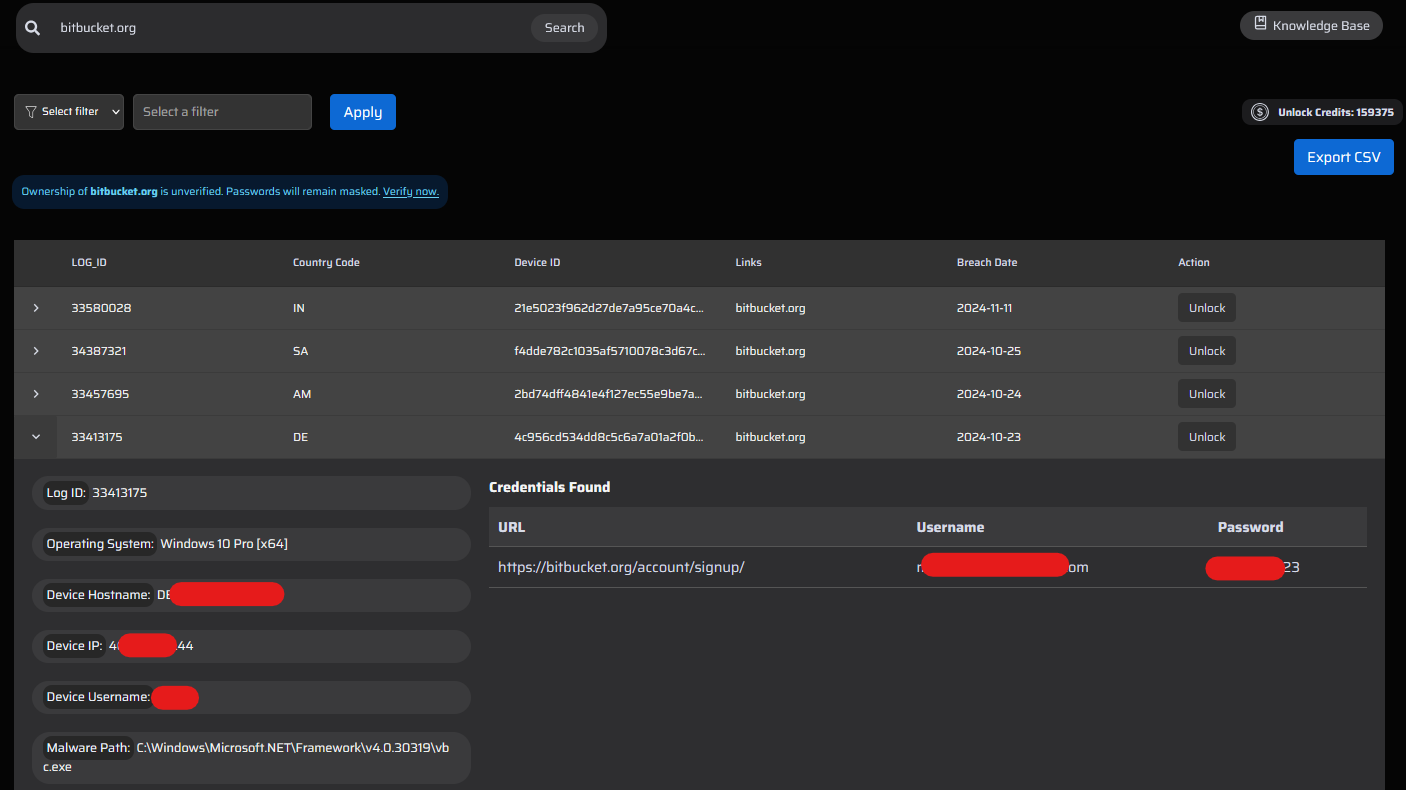
Identifying SaaS Instances and Hidden Login Pages
To maximize your findings:
- Enumerate Paths: Use tools like ffuf and GoBuster to scan for login endpoints such as
/login,/login.do,/admin, and/auth. - Detect Authorization Redirects: When you encounter a redirect to Microsoft or other identity providers, it’s crucial to continue probing for alternate login pages that may bypass the SSO layer.
Example Workflow:
- Use Subfinder to gather subdomains
subfinder -d company.com -o subdomains.txt
- Filter results with
grepfor known SaaS and CI/CD patterns:
cat subdomains.txt | grep -E 'atlassian\.net|servicenow\.com|salesforce\.com|jenkins\.company\.com' > potential_targets.txt
- Enumerate paths on those subdomains with ffuf:
ffuf -u https://potentialtarget.com/FUZZ -w /path/to/wordlist.txt -mc 200,302
No Results? Try This:
If initial subdomain enumeration yields no results, directly enumerate subdomains for popular SaaS domains to discover potential instances related to your target. For example:
- Use Subfinder directly on the SaaS domain
subfinder -d <SaaSDomain.com> -o saas_subdomains.txt
- Search for your target’s name within these subdomains:
cat saas_domains.txt | grep "targetname"
This approach helps uncover potential subdomains or related assets that may not be directly visible under the main company domain but are hosted under the SaaS provider's domain.
Add a little bit of Sauce - Search with WhiteIntel
WhiteIntel.io provides powerful search capabilities that allow you to search by domain names, subdomain names, and email addresses. With our advanced search filters, you can quickly identify affected SaaS credentials related to your bug bounty target. For instance, if you are investigating bitbucket.com, you can use our subdomain filter to check if any credentials associated with your target’s name are present. This streamlined approach helps you uncover valuable data efficiently and focus on high-impact findings.
Alternatively, you can use our affected URLs search feature to investigate whether any notable URLs have been involved in a breach. This helps you quickly identify valuable leads and potential vulnerabilities related to your target.
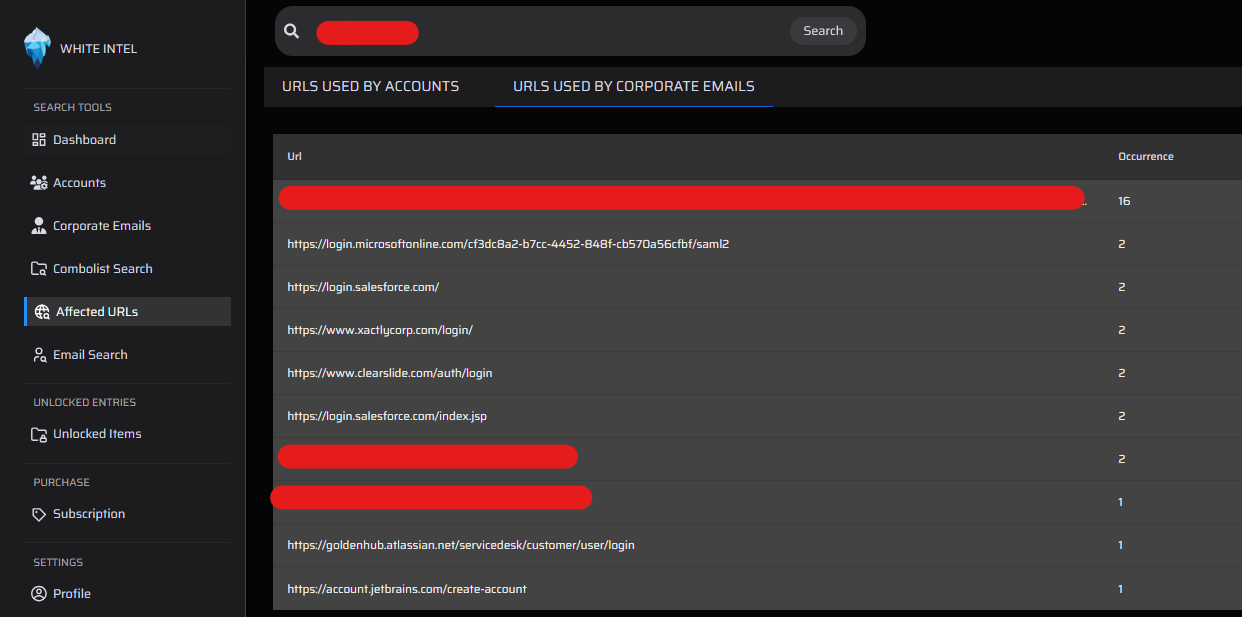
Additional Tips
For internal applications or SaaS web panels, employees may sometimes use usernames without corporate email extensions. In such cases, ensure to review both the "Account" leaks and the "Corporate Emails" sections, using the detected potential panel domain addresses for verification.
Reporting
Sample Report Template for Submission
Title: [Unauthorized Access to [SaaS/CI/CD Panel] for [Target Name]]
Summary: A vulnerability was discovered on [e.g., jira.company.atlassian.net] using leaked credentials and OSINT tools. This vulnerability allows unauthorized access to sensitive project data and user information.
Details:
- Asset Type: [e.g., Jira panel, Jenkins server]
- Discovery Method: Combination of leaked credentials and OSINT tools such as Subfinder and Shodan.
- Login Endpoints Found At: [e.g.,
/login,/login.do] - Compromised Credentials: USERNAME, PASS
Additional Details for Incident Response Process
- Date of Infection: [Date of Infection]
- Compromised Hostname: [Compromised Hostname]
- Compromised Username: [Compromised Username]
- Compromised Device IP: [Device IP]
- Malware Path: [Malware Path]
Steps to Reproduce:
- Access
jira.company.atlassian.net. - Log in using verified credentials [following ethical guidelines].
- Note the presence of sensitive data or admin access.
Potential Impact: Unauthorized access could lead to data exposure, code leaks, or operational disruptions.
Suggested Mitigation:
- Enforce MFA on all login portals.
- Regularly monitor for reused credentials.
- Harden paths and conduct regular security audits.
Supporting Evidence: [Attach sanitized screenshots, proof of concept, and relevant logs.]
How WhiteIntel Helps Bug Bounty Researchers
WhiteIntel is committed to empowering bug bounty researchers by providing them with the tools and data necessary to elevate their game. Our newly launched Researcher License is tailored specifically for verified bug bounty hunters, offering them exclusive access to WhiteIntel's comprehensive services.
- Access to Extensive Breach Data: Researchers can leverage our detailed breach data, including leaked credentials and stealer logs, to cross-reference and discover potentially vulnerable assets related to their bug bounty targets.
- Advanced Search Features: WhiteIntel’s platform allows for deep and targeted queries, helping researchers identify compromised accounts and assess the security posture of scoped targets.
- Complementary OSINT Integration: The platform works seamlessly alongside other OSINT tools, aiding in the identification of subdomains and exposed services to enhance the discovery process.
- Real-Time Updates: Users benefit from timely notifications on new data breaches and credential leaks, ensuring they stay ahead in their research and reporting.
- Ethical and Compliant Data Use: We ensure that all data provided through our platform adheres to the highest standards of ethics, supporting responsible disclosure and legal research practices.
Enhancing Bug Bounty Success:
WhiteIntel’s Researcher License enables bug bounty hunters to:
- Deepen Their Investigations: Utilize access to unique data sources to uncover previously hidden attack vectors.
- Save Valuable Time: Accelerate the discovery process for vulnerabilities that could take days or weeks to identify without these resources.
- Submit High-Impact Reports: Demonstrate comprehensive findings, showcasing unauthorized access to systems or sensitive data using validated and responsible methods.
The Researcher License is offered exclusively to verified bug bounty hunters who commit to ethical hacking and responsible disclosure practices. WhiteIntel is proud to support the security research community by equipping them with the tools to make more impactful discoveries and contribute to a safer digital ecosystem.
To learn more about the Researcher License contact us via Contact Form and take your bug bounty hunting to the next level.
whiteintel.io