Exposing Threat Actors with Whiteintel AI

Beyond Breach Monitoring: How Neural Identity Attribution is Closing the Gap Between a Leaked Email and a Physical Identity.
The Irony of Modern Malware
There’s a poetic irony in modern cybercrime: threat actors often end up infecting themselves. Whether it’s a developer testing out a new ransomware build, a 'stealer' double-checking their work, or just a script kiddie who accidentally double-clicked their own payload, these self-infections are the ultimate intelligence goldmine.
When a criminal’s own machine gets hit, it spills their entire digital life. Suddenly, you aren’t just looking at anonymous code; you’re looking into their personal connections, their private apps, and their real-world accounts. It pulls back the curtain on their daily habits and social circles, turning a faceless threat into a real, identifiable person.
Today, we are introducing Investigation+, the new Whiteintel module designed specifically to exploit these operational failures.
Introducing Investigation+: Neural Identity Attribution
Investigation+ isn't just another search tool; it is a forensic engine powered by Whiteintel AI. By indexing one of the largest infostealer datasets in the world, we don't just find stolen data, we uncover the Identity behind the attack.
How It Works: Turning Telemetry into Identities
When an identity is resolved through Investigation+, our niche AI implementation performs a deep-trace analysis of the exfiltrated logs.
1. Identity Resolution (Real Names & Phone Numbers)
Whiteintel AI doesn't stop at an email address. It correlates data across thousands of logs to find where that same actor might have used a real name, a phone number, or a government ID for a legitimate service (like a food delivery app or a personal social media account) from the same infected machine.
2. The Power of Niche AI
Our AI is specifically trained on the "logic of a log." It understands the difference between a random victim and a threat actor testing their own tools. By analyzing specific patterns in the exfiltrated data—such as the presence of malware development tools or access to C2 panels—it prioritizes the Attribution of high-value targets.
Why Investigation+ is a Game Changer for Analysts
- De-anonymization: Move from an alias to a physical person in seconds.
- Asset Prioritization: Use AI-driven scoring to understand which assets are most critical.
- Comprehensive Datasets: Access massive telemetry that includes leaked names, phones, and even Govt IDs recovered from the dark web.
A Case Study: Uncovering the Rey of SLSH
Disclaimer: The data and case study presented herein pertain to a threat actor whose activities and identity have been previously disclosed by other security researchers and are currently available in the public domain.
The most prominent example of the "Self-Infection Trap" is the case of the threat actor known as "Rey." As a core member for the notorious Scattered Lapsus$ Hunters (a merger of Scattered Spider and LAPSUS$), Rey was responsible for high-profile breaches against global giants like Salesforce and Qantas.
Despite his group's sophistication in social engineering, Rey fell victim to the same tool he weaponized: the infostealer.
The Attribution Path:
- The Mistake: Rey accidentally ran a info stealer on a device he used for both personal and cybercrime operations in late 2023 and early 2024.
- The Metadata: The resulting stealers to collect his stored credentials related to his username
o5tdev. - The AI Correlation: By using the comprehensive data sets and niche AI implementation, Whiteintel was able to uncover malicious connections.
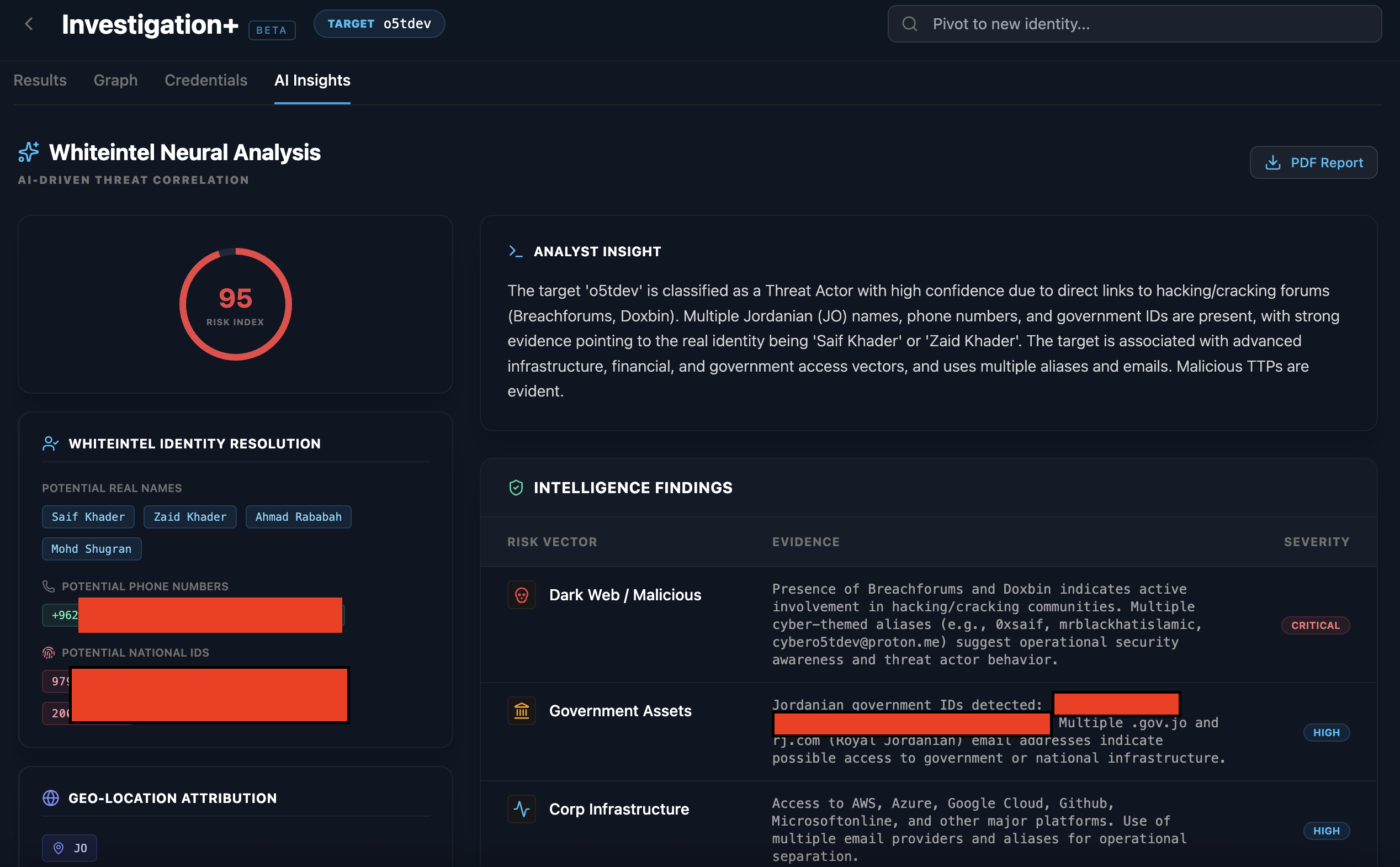
- The Result: The core member of the threat actors group was revealed to be Saif Al-Din Khader, a teenager operating out of Amman, Jordan.
The Mistake and The Metadata
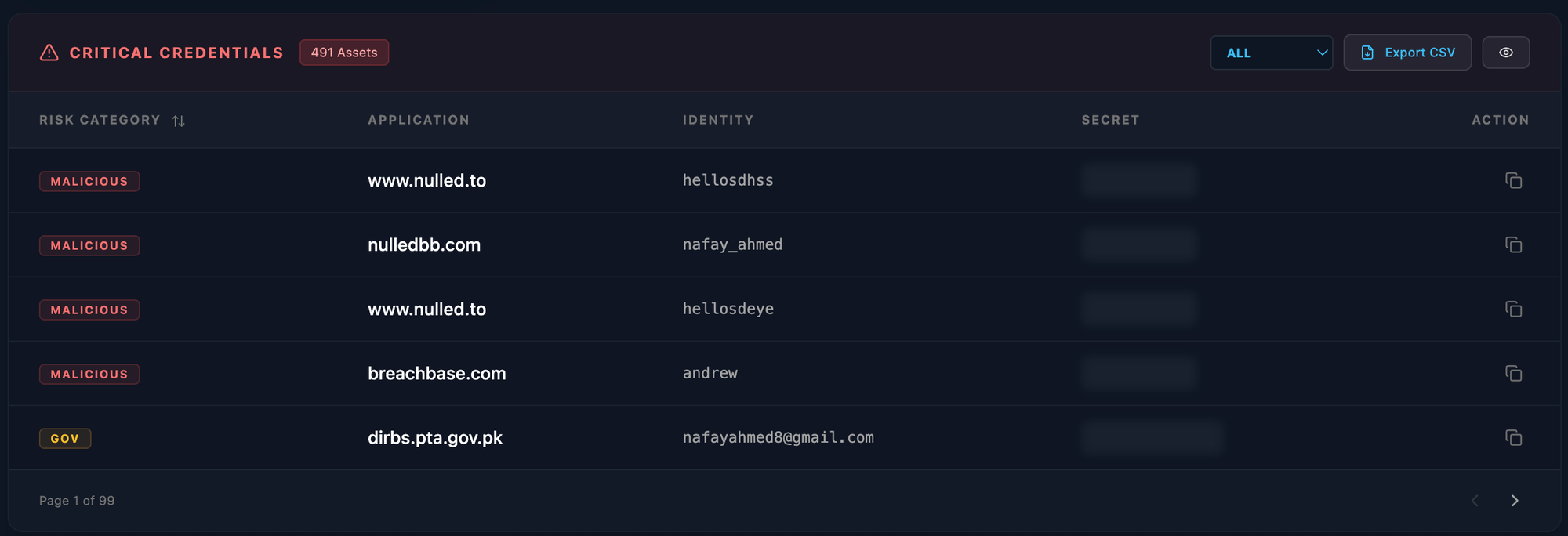
On Dec 17 2023 and February 2, 2024, WhiteIntel documented a critical OPSEC failure by the threat actor "Rey." A self-infection incident involving information-stealing malware exposed a primary username, establishing a definitive link to their real-world identity. Subsequent forensic analysis uncovered an additional 69 accounts and 98 passwords captured from the same compromised devices.
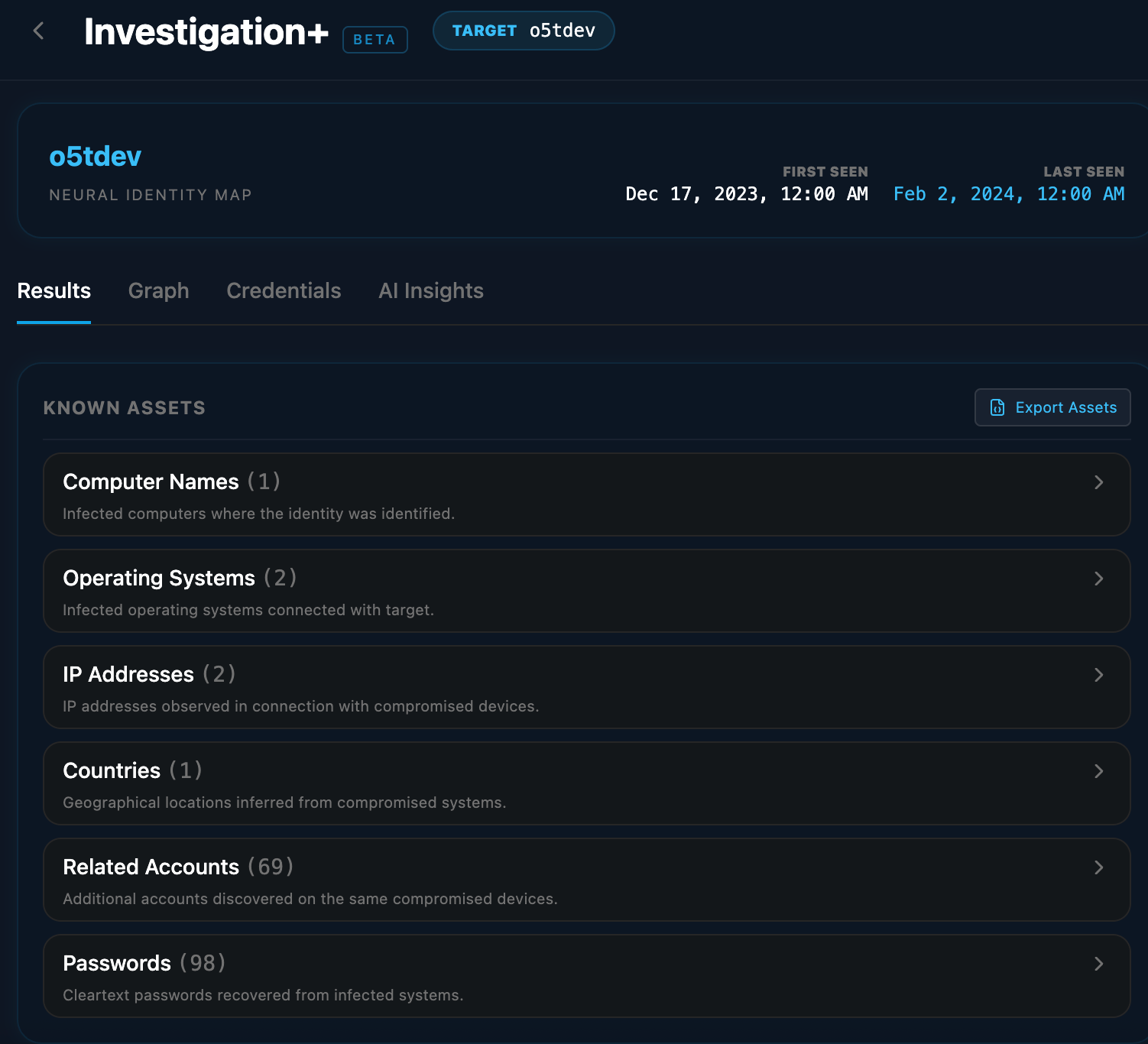
The specified username has been observed in 2 stealer infections.
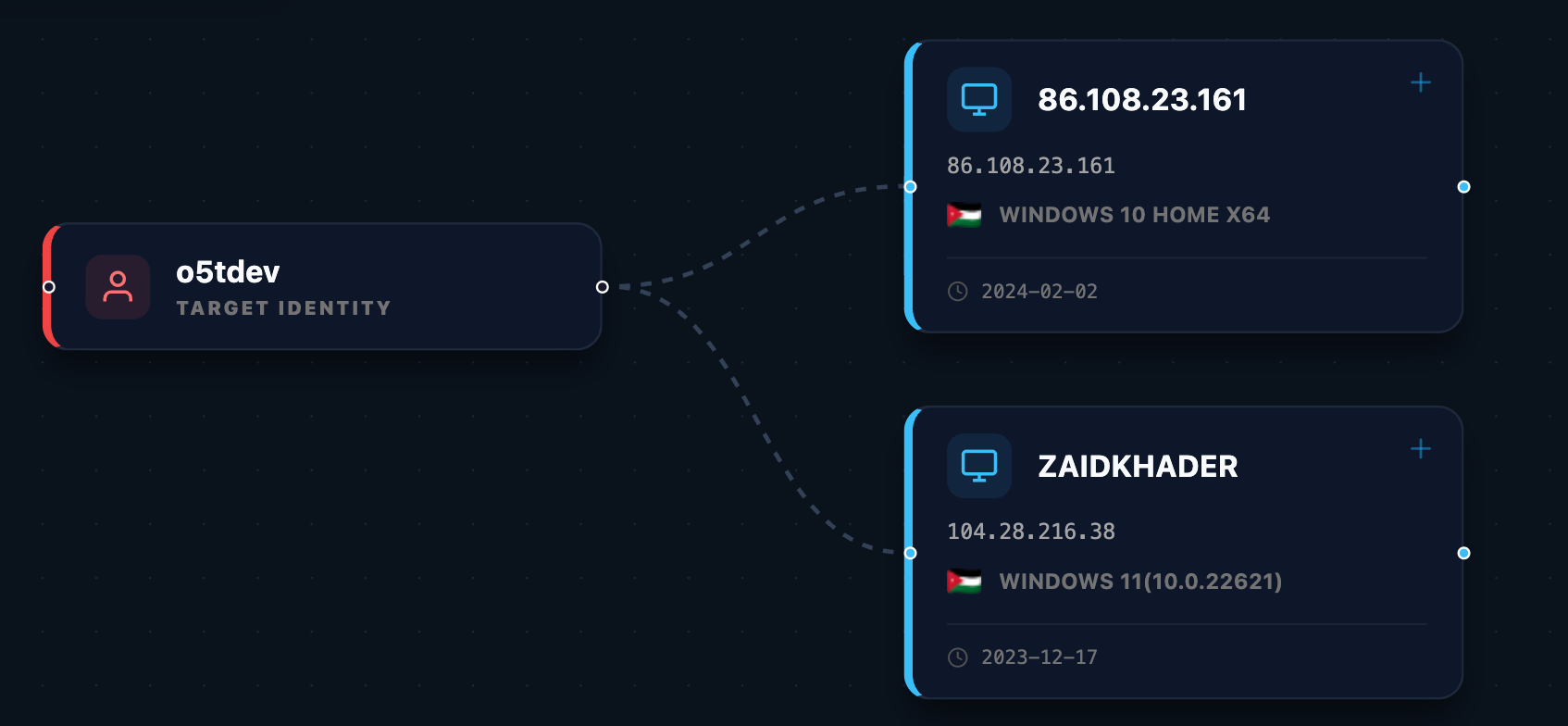
The resulting telemetry from this infection provided a wealth of forensic evidence. The information stealer successfully exfiltrated a diverse array of linked accounts and cleartext passwords, including active credentials for high-profile hacker forums—such as BreachForums—and several other known malicious domains. These logs revealed a complex web of unique usernames, providing the first clear look into the actor's multi-platform digital footprint.
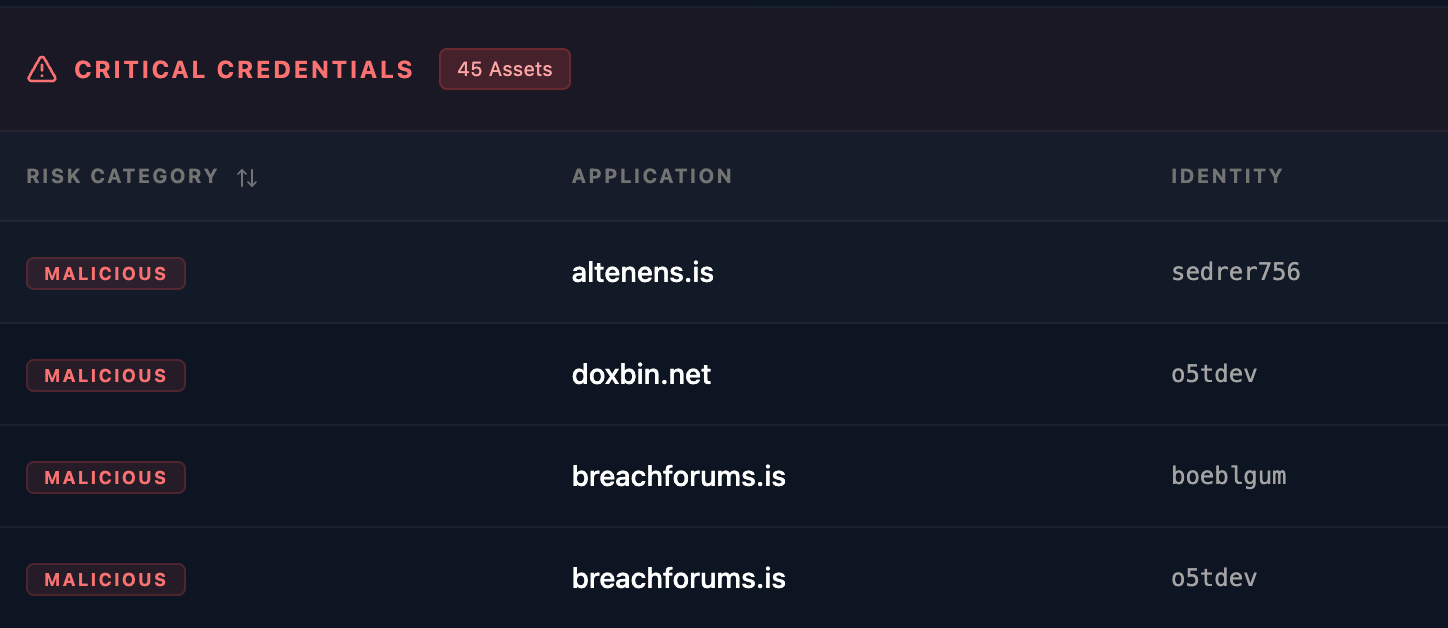
The AI Correlation
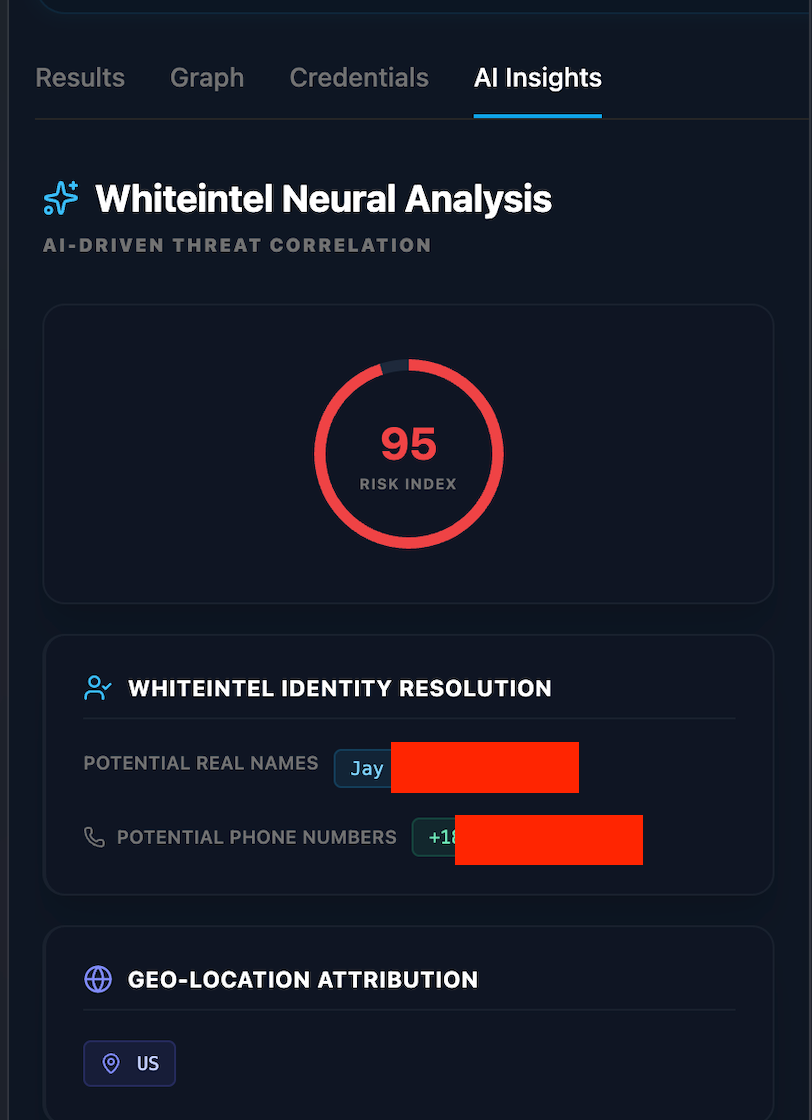
Through the use of the exfiltrated telemetry, Whiteintel AI successfully identified that the same infected device was used to access highly sensitive sectors. Our neural correlation uncovered repeated access to Governmental portals, Financial institutions, and Cryptocurrency platforms, providing definitive proof of the actor’s high-value digital footprint.
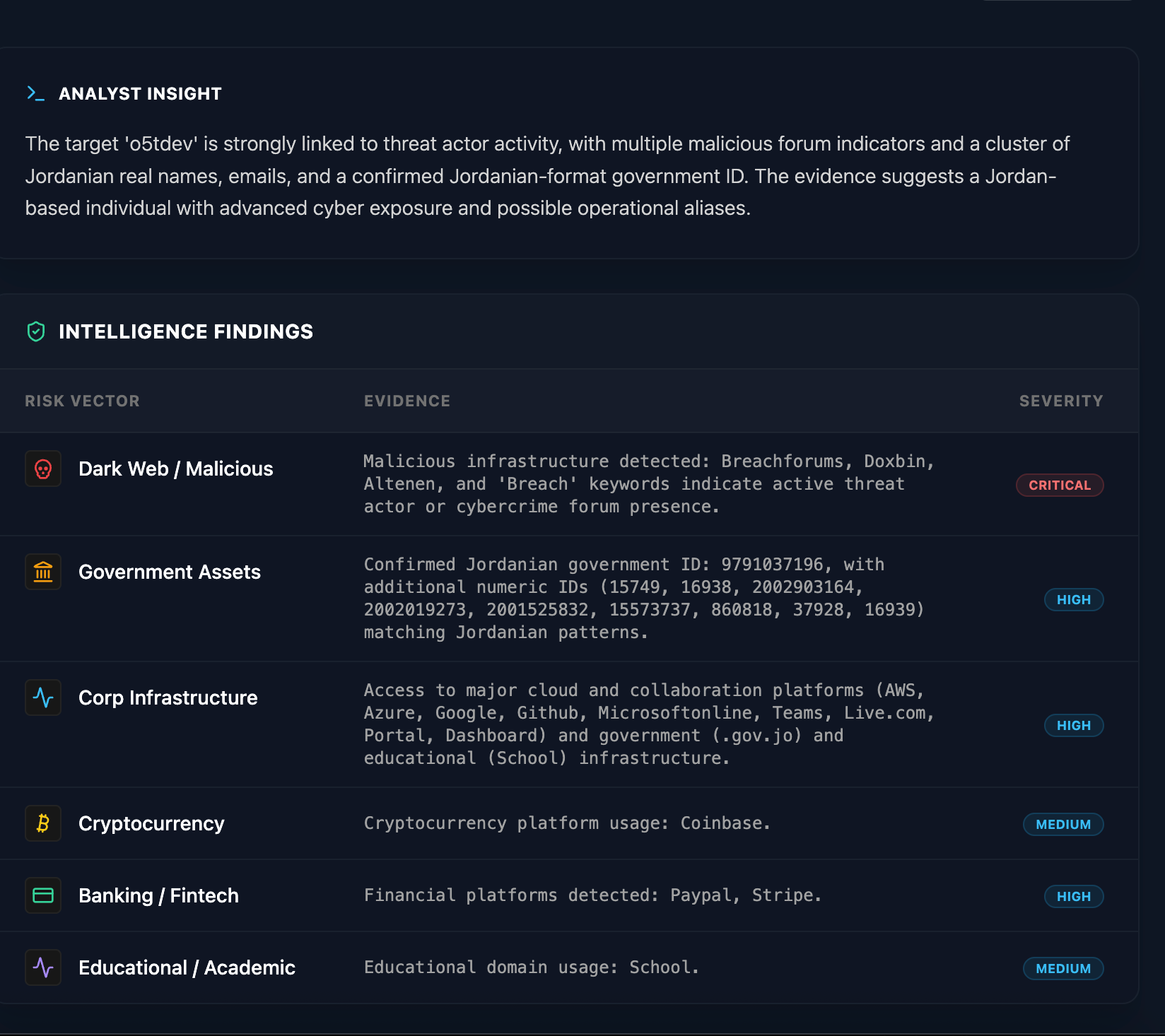
By correlating the unique usernames used across critical applications, Whiteintel AI successfully performed a deep-trace attribution. Our neural models pivoted from these digital aliases to uncover Suspected Real Names, Potential Phone Numbers, and even Governmental IDs. This forensic resolution effectively stripped away the layers of anonymity, linking the actor's underground persona to a verified physical identity.
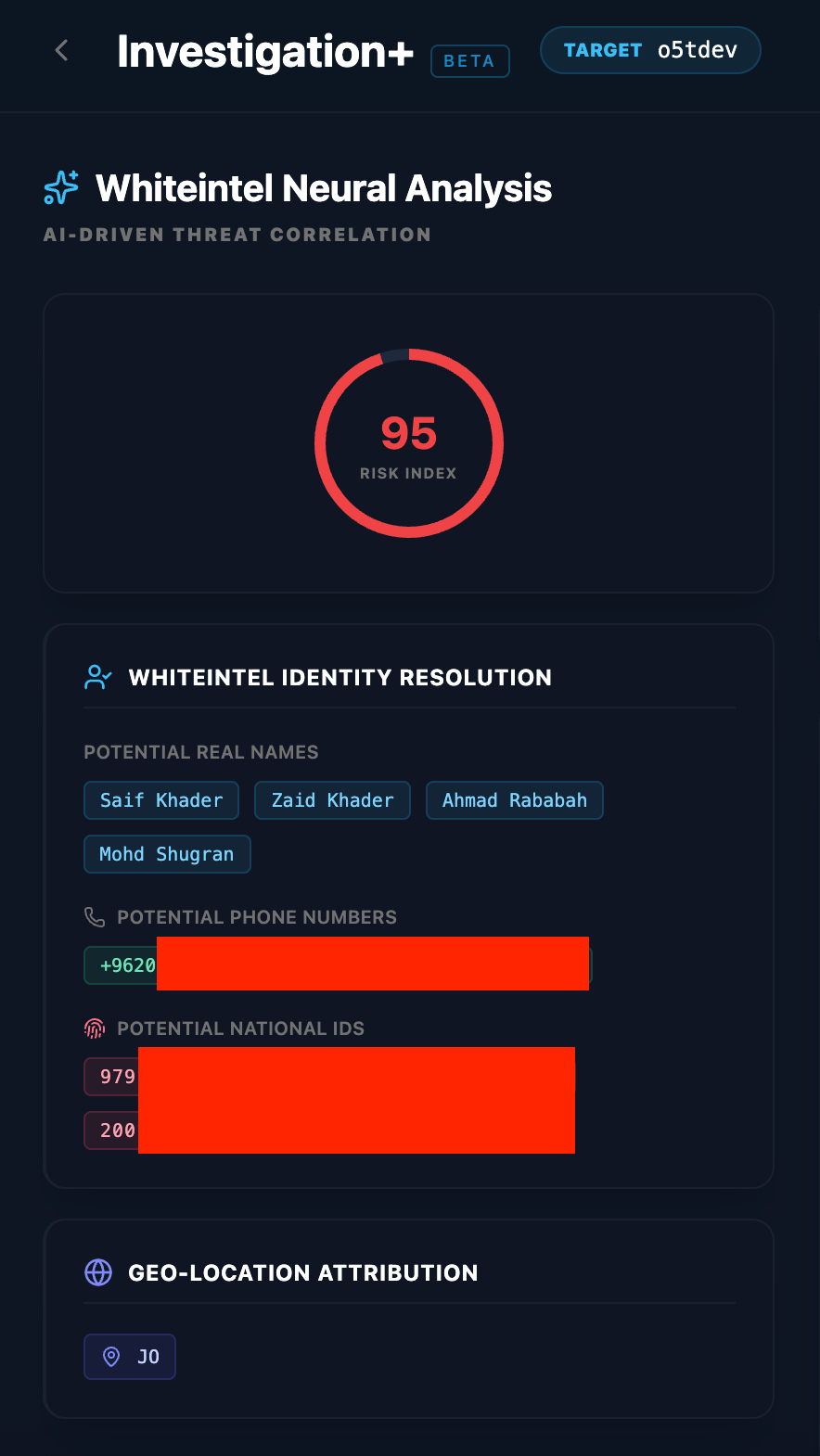
The Results: Neural Identity Resolution
Unlike traditional threat intelligence approaches that rely on static indicators and manual cross-referencing, Whiteintel AI utilizes a massive, proprietary dataset combined with a niche AI implementation designed specifically for forensic attribution.
By ingesting raw infostealer telemetry, the system doesn't just "match" data—it reconstructs digital personas. In the study of the actor "Rey," this meant moving beyond a leaked username and into a comprehensive identity profile.
About Investigation+ Module
The Investigation+ Module is Whiteintel.io's advanced forensic analysis suite, specifically engineered for high-fidelity identity attribution and threat actor unmasking.
While Whiteintel provides baseline monitoring for researchers and enterprises, the Investigation+ module is the "Neural engine" of the platform, exclusively reserved for Threat Intel (TI) License holders. It is designed for SOC teams, federal investigators, and high-level threat researchers who need to bridge the gap between anonymous malware telemetry and physical identities.
For more information about Whiteintel see: whiteintel.io
Official feature documentation: https://knowledge.whiteintel.io/white-intel-usage/investigations+-beta