Rebranded WhiteIntel Platform
We’ve been working on something big—and it’s finally here.
We’re incredibly excited to introduce the newly rebranded WhiteIntel platform, designed from the ground up to give you a faster, smoother, and smarter experience when tracking threats and breaches across the dark web.
Why the Change?
Over the past year, we’ve grown alongside our users—listening to your feedback, learning how you use the platform, and identifying areas where we could do better.
So we made some big moves:
- We redesigned the entire dashboard interface to be cleaner and more intuitive.
- We drastically improved search performance, so results come in faster—especially for large watchlists.
- And most importantly, we’ve enhanced how you filter, view, and dive into breach data—making it easier to investigate what matters most to your organization.
What’s New?
Lightning-Fast Search
Searches that once took several seconds now return results almost instantly. We’ve optimized both frontend and backend performance, especially for users with large datasets.
Smarter Filters & Navigation
We’ve improved global search filters to be more powerful yet easier to use. Want to find everything tied to a single domain? Or filter by breach type or log date? You’ve got it—all with a few clicks.
Clearer Incident Views
The new incident pages are more informative, neatly organized, and easier to act on. Less clutter, more context.
New Look, Same Mission
You’ll notice our updated branding too—simple, sharp, and aligned with our focus on transparency, speed, and reliability.
Introducing Our New Plans
- Trial – A free way to explore the platform and get a feel for what’s possible. No strings attached.
- Researcher – Ideal for individuals or teams conducting threat research, investigations, or academic work.
- Enterprise – Built for organizations that need broader visibility across attack surfaces and internal exposure.
- Threat Intelligence – The full package, with deeper breach data, enriched context, and advanced features tailored for security teams and CTI analysts.
Full details and feature comparisons for each plan will be shared shortly in a dedicated breakdown.
KYC & Responsible Use
As part of our commitment to ethical data usage, we’ve also introduced a KYC (Know Your Customer) verification process.
This replaces the old domain verification system and allows us to onboard organizations and individuals more flexibly—but with greater responsibility.
Access to certain data types is now restricted to verified users with legitimate, white-hat intent. If you’re here to defend, protect, and investigate—we welcome you with open arms. 🫡
👀 Let’s Take a Look
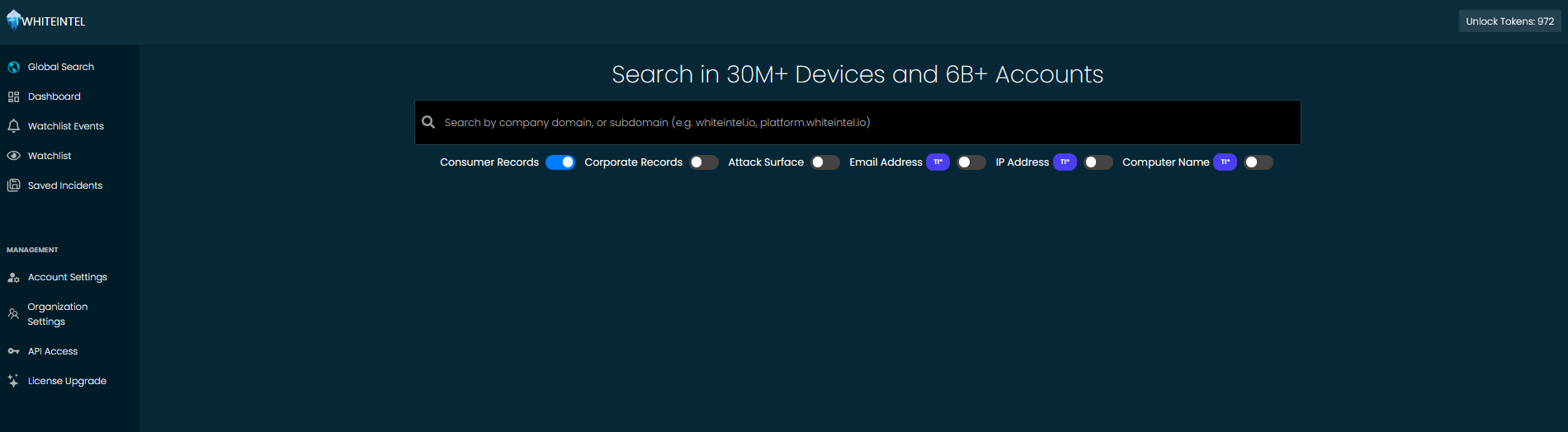
Here’s a sneak peek at the newly redesigned Global Search experience inside WhiteIntel.
In this example, we’re searching for breaches related to tesla.com. With access to over 30 million devices and 6 billion+ leaked accounts, results appear in real-time and are broken down by:
- Leaked Account Details (with smart masking for privacy)
- Associated Applications where credentials were found
- Date Last Seen in breach logs
- Breach Type, like
stealerorcombolist
We’ve also made it easier to filter results across multiple data types—such as Consumer Records, IP Addresses, Email Addresses, and Computer Names—with a single toggle. Some of these filters are marked with a TI badge, meaning they require a Threat Intelligence license to access.
And with a click of Export CSV, you can quickly extract and analyze the findings in your preferred tools.
All of this happens within a clean, focused UI—built to help you investigate faster and take action with confidence.
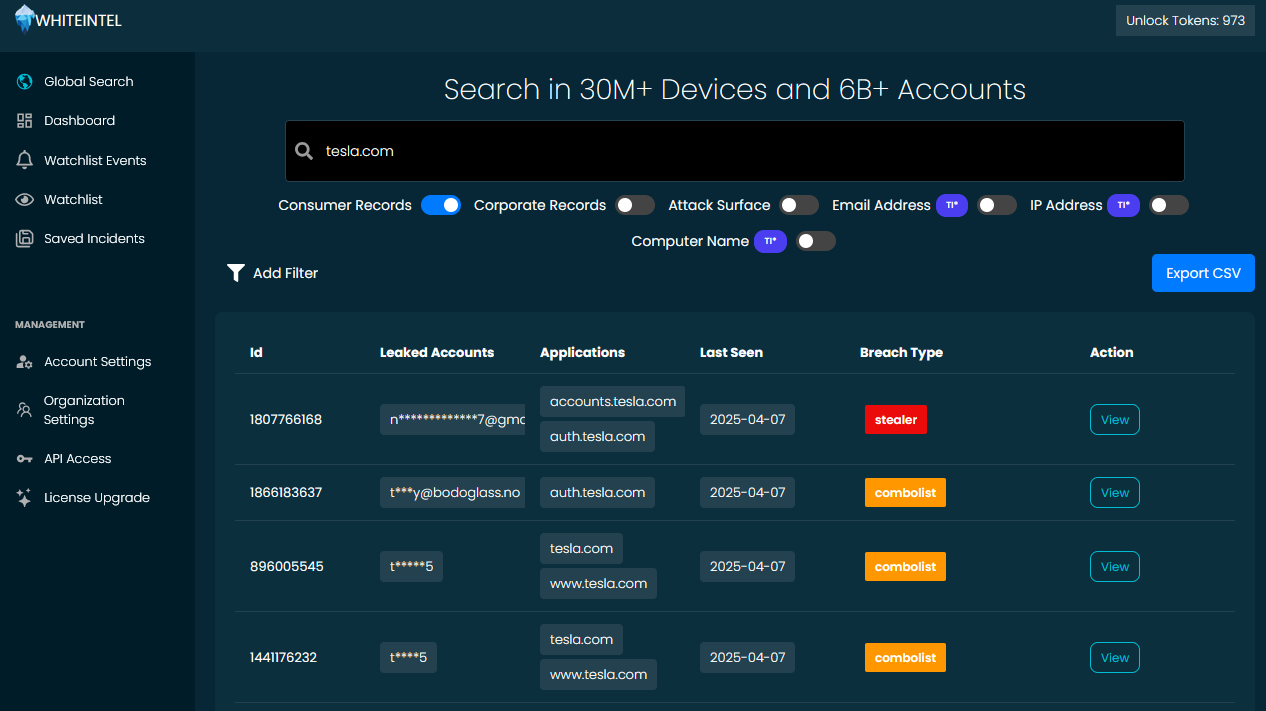
🔍 Dig Deeper with Advanced Breach Insights
When a breach is detected, surface-level details aren't enough. That’s why we’ve built Advanced Insights—a new, deeper view into each compromised account on WhiteIntel.
In the example above, you're seeing a detailed incident view for a credential leak tied to a Tesla-related application. Here's what users can now access:
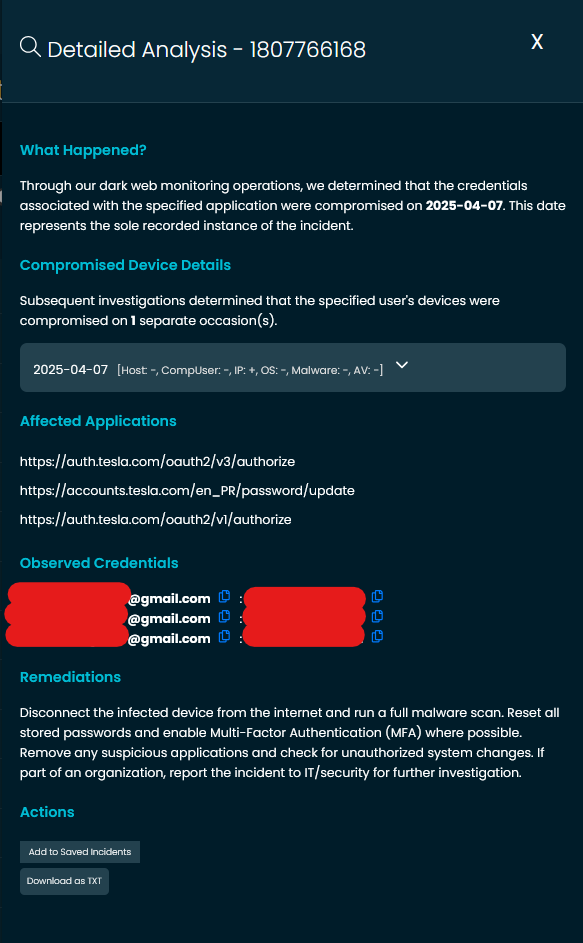
🧠 What You’ll Learn:
- What Happened?
A clear timeline of when the credential was first observed in our dark web monitoring systems—giving you instant context for the compromise. - Compromised Device Details
Our system correlates breaches to the specific device(s) where the credential was captured, including details like host, IP, and system environment (when available). - Affected Applications
All URLs related to the breach are listed for reference, investigation, or internal alerting. - Observed Credentials
See exactly which usernames and passwords were leaked (masked in UI for safety)—alongside one-click copying for security teams needing to take action fast.
📥 Export & Take Action
Click "Download as TXT" to export the incident data for recordkeeping, offline use, or integration into your own workflows. You can also instantly save incidents to your dashboard for future reference or reporting.
🛡 Recommended Remediations
Each incident now comes with tailored remediation steps to guide response—whether you’re securing a personal account or coordinating with your organization’s security team.
📊 Your Exposure at a Glance
Say hello to the new WhiteIntel Dashboard—a powerful command center that gives you a bird’s-eye view of your organization’s breach exposure across the dark web.
In this example, we're looking at results for tesla.com, and here's what the dashboard reveals:
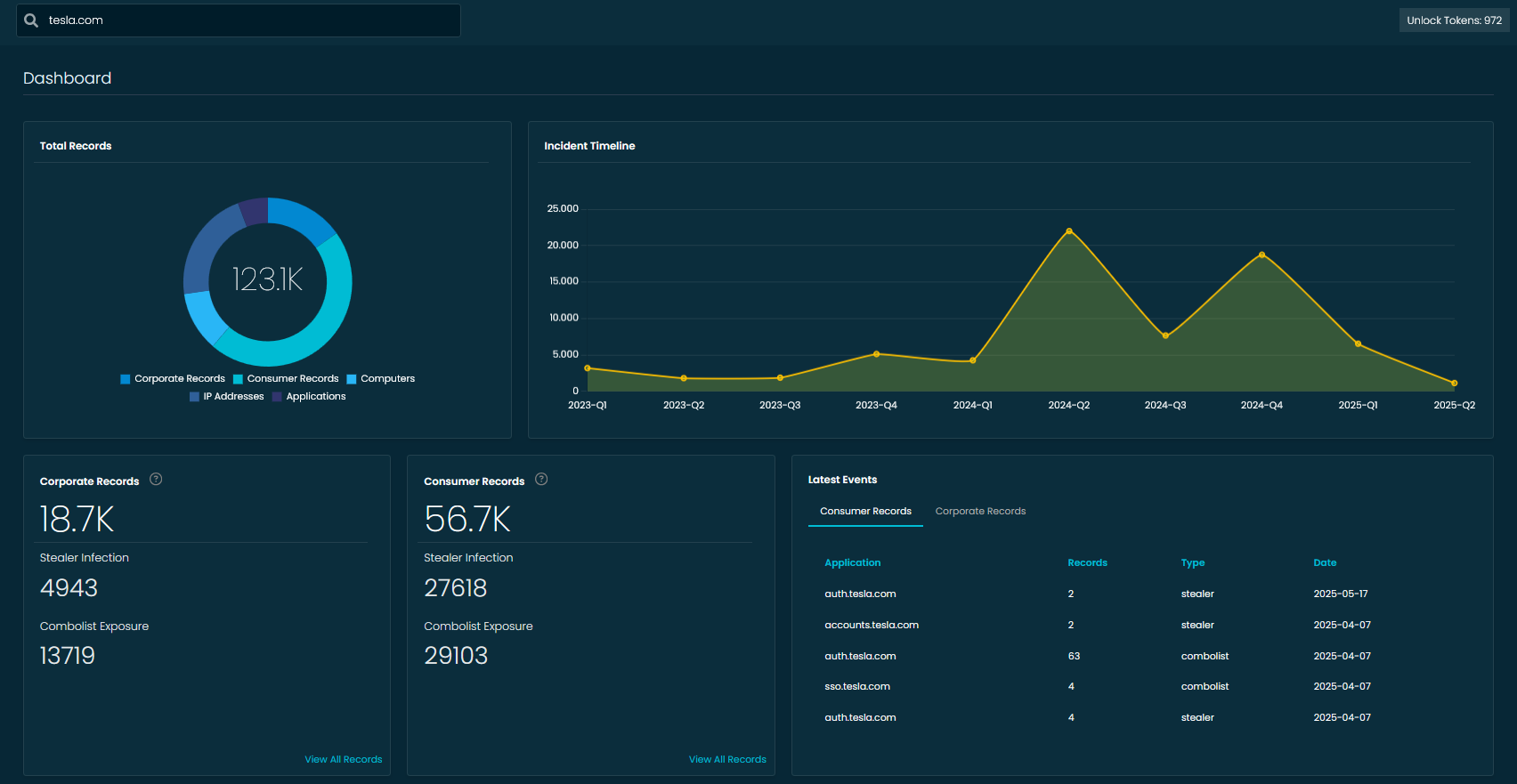
🔄 Total Records Breakdown
At the heart of the dashboard is a donut chart showing the total number of exposed records (123K+), broken down by:
- Corporate Records
- Consumer Records
- Exposed Devices (Computers)
- IP Addresses
- Applications
With one glance, you know what kind of data is exposed—and how much of it.
📈 Incident Timeline
See how breach activity has changed over time. The timeline graph highlights spikes and patterns in exposure, helping you correlate activity with known campaigns or incidents. For example, Q2 2024 and Q4 2024 show major upticks—worth investigating.
🔍 Record Categories
Below the chart, you get a deeper breakdown:
- Corporate Records: 18.7K exposed — including 13.7K from combolists and nearly 5K from stealers.
- Consumer Records: 56.7K exposed — split almost evenly between stealer infections and combolist leaks.
Each box links you to a full record view for further investigation.
🧩 Latest Events
On the right, the dashboard highlights the most recent events, showing which apps were targeted, how many records were exposed, and what type of breach (e.g., stealer or combolist). It’s your real-time feed for emerging threats.
👁 Stay Ahead with Your Watchlist
With WhiteIntel’s new Watchlist, staying on top of what matters most to your organization just got easier.
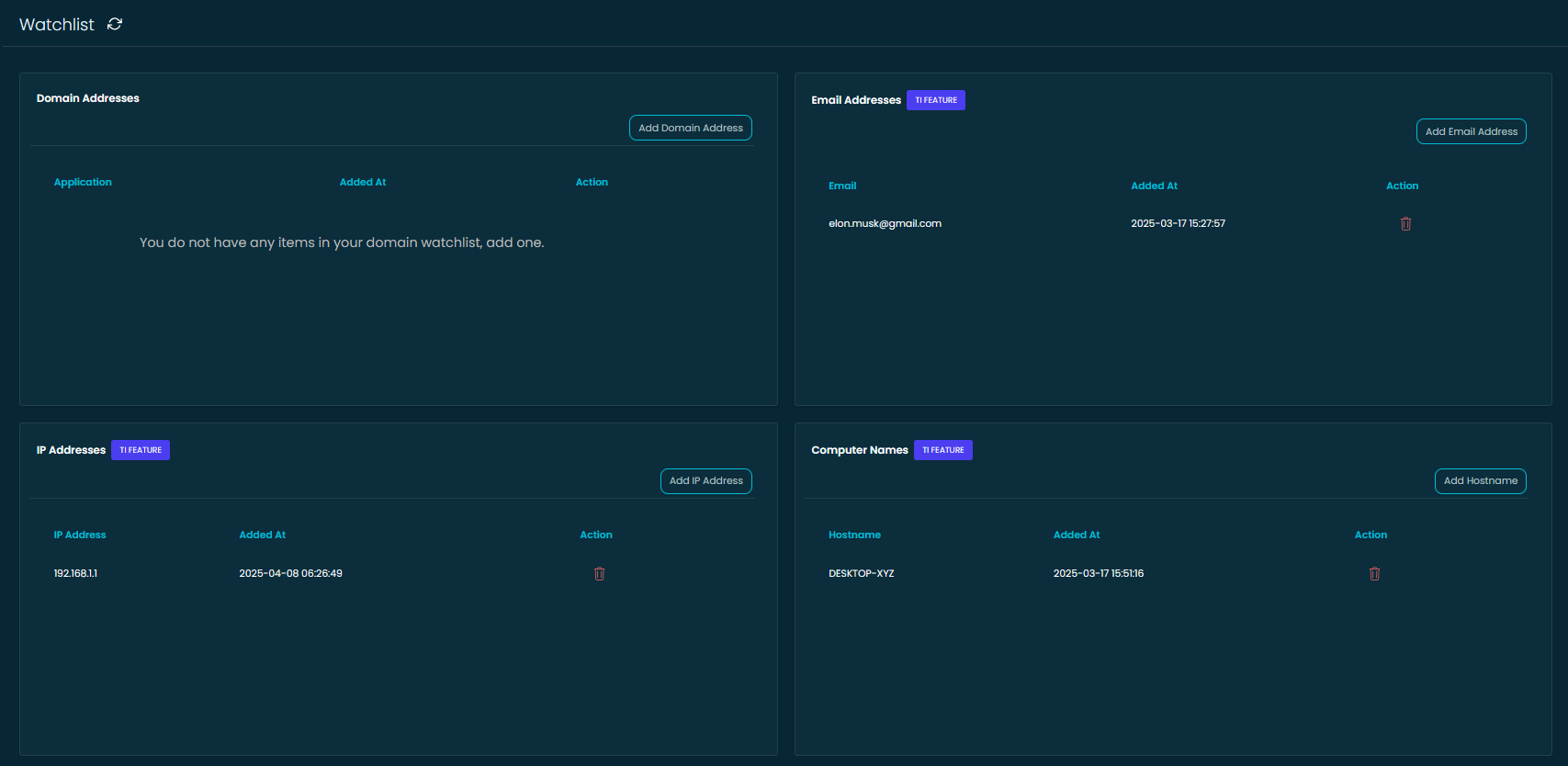
This section allows you to monitor specific assets—like domains, email addresses, IPs, and hostnames—and be instantly alerted if any of them are identified in breach data across our platform.
🧩 What You Can Track:
- Domain Addresses – Perfect for protecting your brand and employees’ accounts.
- Email Addresses – Get notified if sensitive inboxes (like execs or IT accounts) appear in leak data. (TI feature)
- IP Addresses – Monitor known internal or cloud infrastructure IPs for any exposure. (TI feature)
- Computer Names – Identify if specific device hostnames show up in breaches. (TI feature)
Each entry shows exactly when it was added, and with one click you can remove outdated items or add new ones.
🚨 Why It Matters
The Watchlist acts like your personal threat radar. It continuously scans new breach records and flags anything relevant to what you’ve added—saving you time, increasing visibility, and helping you respond before threats escalate.
✨ Some asset types (like IPs and hostnames) are part of our Threat Intelligence tier, designed for more advanced users and teams.
🔔 Real-Time Breach Alerts with Watchlist Events
The Watchlist Events page is your real-time feed for anything that matters to you. As soon as a domain, email address, IP, or hostname on your Watchlist is observed in a breach, it appears here—timestamped, categorized, and ready for review.
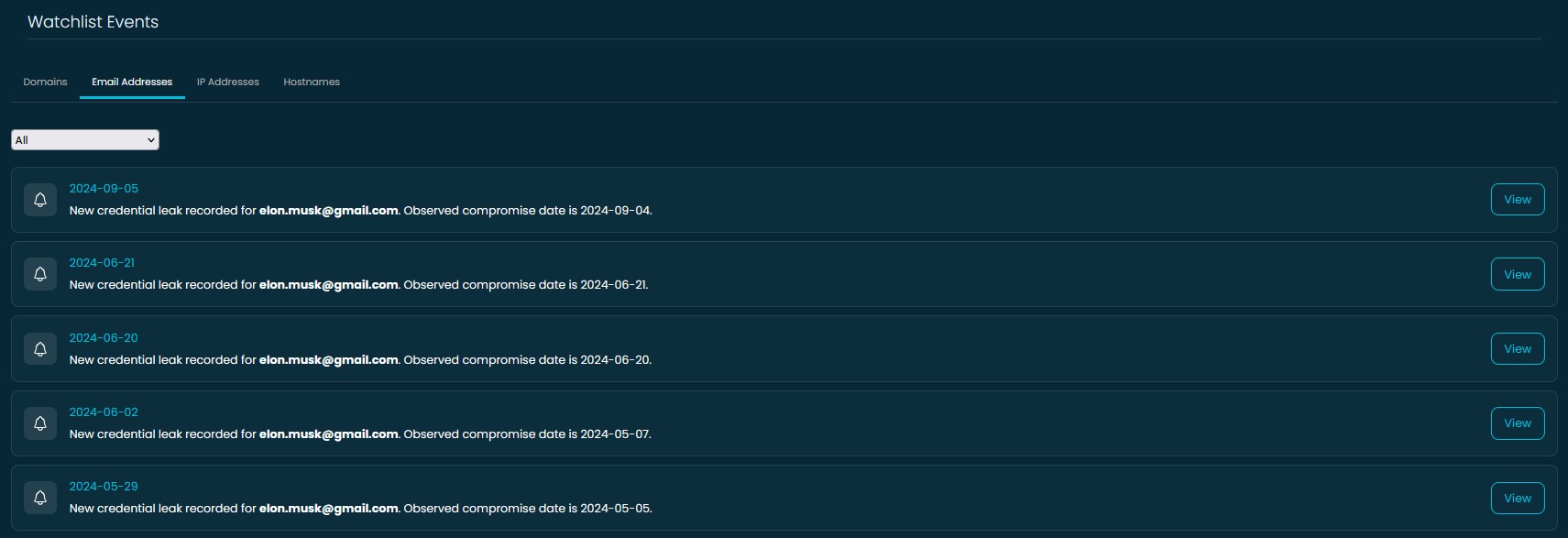
In this example, we’re tracking a specific email (elon.musk@gmail.com), and we can see a series of credential leaks recorded across multiple dates. Each event entry includes:
- The date we detected the breach
- The estimated compromise date
- A View button to dive deeper into the incident details
🧠 Why It Matters
Rather than digging through thousands of records manually, Watchlist Events bring the threats to you. It’s proactive monitoring in action—helping you stay ahead of incidents and reduce your reaction time.
Just add the items you want to monitor, and let WhiteIntel do the watching.
📝 Organize and Track with Saved Incidents
Security investigations don’t always happen in one sitting. That’s why we introduced Saved Incidents—a space where you can bookmark important breach cases and come back to them when you're ready to dig deeper.
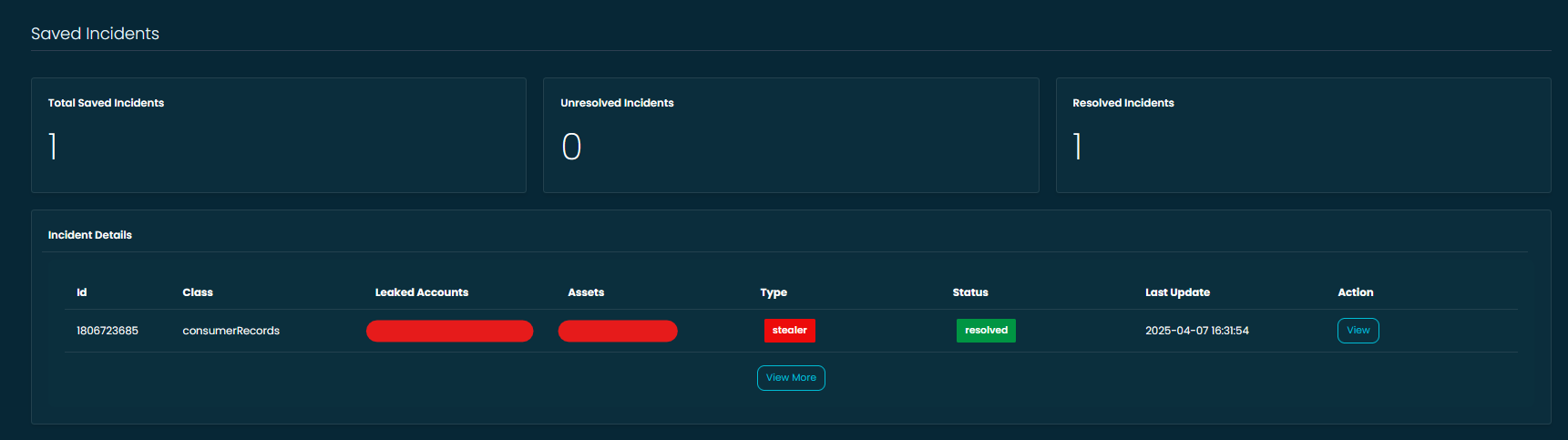
From this dashboard, you can:
- ✅ View your total saved incidents
- 🚧 Track which ones are still unresolved
- ✅ Mark completed ones as resolved
In the example above, a stealer-type incident involving leaked consumer credentials has already been reviewed and resolved. With one click, analysts can open incident details, add internal notes (if needed), or change the status based on the investigation's outcome.
🔁 Your Incident Workflow, Simplified
Whether you’re triaging multiple threats or collaborating with a team, Saved Incidents gives you a clear and organized workflow. Keep things moving—and never lose sight of what still needs attention.
Bonus: You can jump back into any incident anytime via the “View” or “View More” buttons.
👥 Manage Your Team with Organization Settings
Collaboration just got easier.
The Organization Settings panel gives you full control over your team’s access, license usage, and account limits—all in one convenient place.
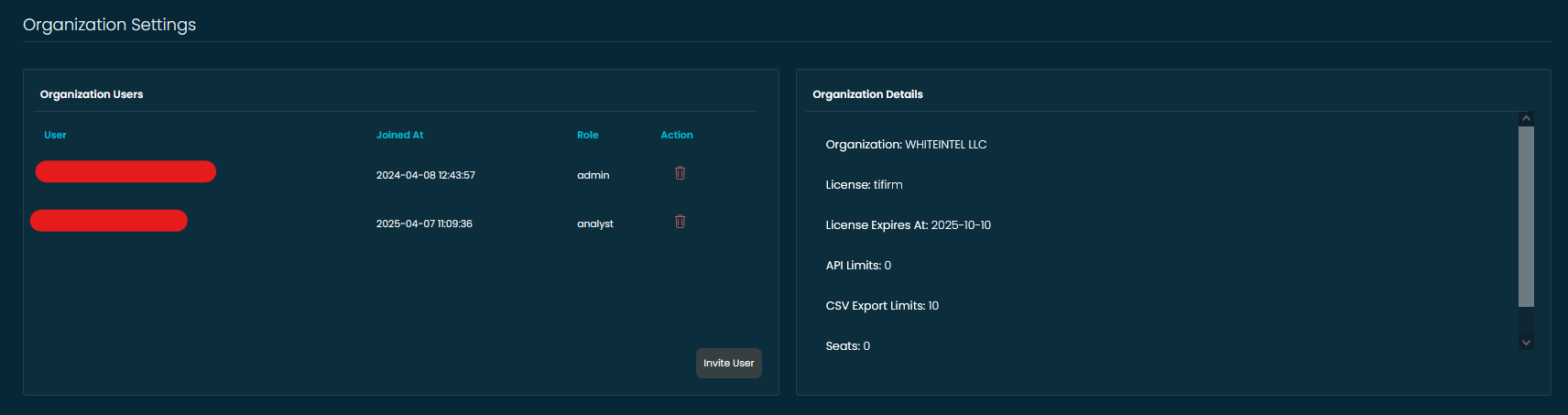
👤 Organization Users
Admins can view all users in the organization, see when they joined, and assign roles such as admin or analyst. Need to onboard someone new? Just hit “Invite User” to send them an access link. You can also remove users at any time with a single click.
🧾 License & Limits
On the right, you’ll find your organization's license type, expiration date, and your current usage limits—including:
- API access
- CSV export limits
- Remaining seats
🪑 Shared Licenses for Teams
Organizations with multi-seat subscriptions can share access across multiple users, enabling analysts, researchers, and security leads to collaborate under one unified license. It’s perfect for firms, security teams, and research groups working together on threat intelligence.
💼 License Plans & Payment Options
We’ve simplified our licensing to better reflect how different users and organizations use WhiteIntel—and we’re excited to share that we now support monthly payments across all plans.
Whether you're a solo security researcher or a large threat intelligence team, there's a plan for you:
🧪 Researcher
$150 / month or $1500 / year + taxes
Perfect for individual cybersecurity experts, bug bounty hunters, and solo investigators.
- 500 data unlocks / month
- Domain, subdomain, and email-based search
- Domain-based watchlist
- Real-time alerts
- 1 seat
- 🔒 Manual KYC (Know Your Customer) required
🏢 Enterprise
$350 / month or $3,000 / year + taxes
Tailored for organizations needing scalable access with automation and export features.
- Unlimited data unlocks
- Domain, subdomain, and email-based search
- Watchlist for domains & emails
- 10 CSV exports / day
- 50 API calls / day
- Real-time alerts
- 2 seats
🧠 Threat Intelligence
$600 / month or $6,500 / year + taxes
Designed for SOC teams and large threat intel groups requiring high-volume access, integration, and resale rights.
- Unlimited data unlocks
- Advanced search: domain, email, IP, computer name
- Full-feature watchlist (email, IP, hostnames)
- 500 CSV exports / day
- 500 API calls / day
- Real-time alerts
- Only plan that allows resale or embedding of WhiteIntel data
- 3 seats
💳 Now Accepting Monthly Payments
Every license type can now be activated with a monthly billing option, making it easier for teams and individuals to get started without long-term commitments.
If you're unsure which plan fits your needs—or want to inquire about custom usage, API scaling, or enterprise deployment—just hit Contact Us and we’ll guide you through it.
Ready to get started?
Sign up for free and see what WhiteIntel can do for you.